System Recovery
Posted: September 3, 2011
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 14 |
| First Seen: | September 5, 2011 |
|---|---|
| Last Seen: | January 8, 2020 |
| OS(es) Affected: | Windows |
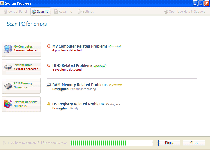 System Recovery is a fake defragmentation program (or defragger) that belongs to the FakeSysDef family. System Recovery creates hostile error messages and a range of other system problems to make it appear as though your PC is seconds away from spontaneous combustion. SpywareRemove.com malware experts haven't found any real error-detection or removal features in System Recovery, let alone actual defragmentation features, and due to these deceitful and outright harmful traits, System Recovery should be considered scamware instead of a legitimate program. Until you delete System Recovery with the appropriate anti-malware product, you should be prepared for attacks that these scamware programs are known for, such as browser hijacks, vanishing files and unwanted changes to your desktop.
System Recovery is a fake defragmentation program (or defragger) that belongs to the FakeSysDef family. System Recovery creates hostile error messages and a range of other system problems to make it appear as though your PC is seconds away from spontaneous combustion. SpywareRemove.com malware experts haven't found any real error-detection or removal features in System Recovery, let alone actual defragmentation features, and due to these deceitful and outright harmful traits, System Recovery should be considered scamware instead of a legitimate program. Until you delete System Recovery with the appropriate anti-malware product, you should be prepared for attacks that these scamware programs are known for, such as browser hijacks, vanishing files and unwanted changes to your desktop.
Staying Alert for System Recovery's Fraudulent PC Monitoring Features
System Recovery, like other FakeHDD rogue defragmenters, pretends to offer many different features that you wouldn't see on a normal defragger, such as RAM analysis and Registry-cleaning. Since these features require extremely specialized functions, SpywareRemove.com malware researchers weren't surprised to discover that System Recovery doesn't have any of the features it advertises, including its supposed defragging function. Instead, these fake features are merely billboards for posting fake warnings.
Many of these errors are also recreated by other rogue defraggers that are related to System Recovery. Examples include System Defragmenter, Ultra Defragger, HDD Control, Win HDD, Win Defrag, Disk Doctor, Hard Drive Diagnostic, HDD Diagnostic, HDD Plus, HDD Repair, HDD Rescue, Smart HDD, Defragmenter, HDD Tools, Disk Repair, Windows Optimization Center, Scanner, HDD Low, Hdd Fix and Win Defragmenter. All of these programs belong to the same overall family of rogue defragmenters as System Recovery and utilize similar attacks.
Finding a Way to Recover Your PC from System Recovery
Gaining access to powerful anti-malware programs is recommended as the first step towards removing System Recovery efficiently. However, System Recovery will create a number of hostile conditions that SpywareRemove.com malware research team has noted may need to be worked around before you can kick System Recovery out of your PC.
- System Recovery may use several methods to hide files on your hard drive, including moving program shortcuts to your Temp folder and attacking Windows Explorer to prevent it from showing certain files. Until you've gotten rid of System Recovery, it's recommended that you try to avoid cleaning out folders casually, since System Recovery may have stored your important files in these locations. If you can't access a critical file, consider using the Command Prompt program, which should show any files that System Recovery tries to hide from Windows Explorer.
- System Recovery may also block security programs. The easiest way to duck under this unwarranted assault is to use Safe Mode or another form of system boot that stops System Recovery from launching in the first place. Because System Recovery, like many other FakeHDD programs, will hook itself into the normal startup routine for your PC, you should assume that System Recovery is active if you've used a normal system boot.
- Finally, web browser redirect attacks are also common with any FakeHDD infection, including System Recovery. Take care to avoid giving away money or private information to websites that System Recovery redirects you to, and never try to buy System Recovery. If necessary, our malware experts have found that you can use the free code '1203978628012489708290478989147' to imitate registration for System Recovery prior to deletion.
Use SpyHunter to Detect and Remove PC Threats
If you are concerned that malware or PC threats similar to System Recovery may have infected your computer, we recommend you start an in-depth system scan with SpyHunter. SpyHunter is an advanced malware protection and remediation application that offers subscribers a comprehensive method for protecting PCs from malware, in addition to providing one-on-one technical support service.
* See Free Trial offer below. EULA and Privacy/Cookie Policy.
Why can't I open any program including SpyHunter? You may have a malware file running in memory that kills any programs that you try to launch on your PC. Tip: Download SpyHunter from a clean computer, copy it to a USB thumb drive, DVD or CD, then install it on the infected PC and run SpyHunter's malware scanner.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%ALLUSERSPROFILE%\Application Data\YvhFlJjjduMa.exe
File name: YvhFlJjjduMa.exeSize: 454.14 KB (454144 bytes)
MD5: cb4a95d5b7068d1f5a189be43469c77c
Detection count: 18
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\Application Data
Group: Malware file
Last Updated: September 5, 2011
%ALLUSERSPROFILE%\Application Data\BvhFlJjjduMa.exe
File name: BvhFlJjjduMa.exeSize: 453.12 KB (453120 bytes)
MD5: 85e8b994c934b8a948e39fec39a0851a
Detection count: 17
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\Application Data
Group: Malware file
Last Updated: September 5, 2011
%ALLUSERSPROFILE%\Application Data\BvhFlJwnduMa.exe
File name: BvhFlJwnduMa.exeSize: 433.66 KB (433664 bytes)
MD5: 16077679cd29b633b380389d192aef56
Detection count: 14
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\Application Data
Group: Malware file
Last Updated: September 5, 2011
%ALLUSERSPROFILE%\Application Data\GyxHFmRWxGIKn.exe
File name: GyxHFmRWxGIKn.exeSize: 453.63 KB (453632 bytes)
MD5: a8e9d0c3e94425633d2a063074170145
Detection count: 13
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\Application Data
Group: Malware file
Last Updated: September 5, 2011
%ALLUSERSPROFILE%\Application Data\iMXxHFmRWxGIKn.exe
File name: iMXxHFmRWxGIKn.exeSize: 464.38 KB (464384 bytes)
MD5: af4c4d542ce33cf71cf2e1fca7953fb5
Detection count: 12
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\Application Data
Group: Malware file
Last Updated: January 8, 2020
%LocalAppData%\[RANDOM CHARACTERS]
File name: %LocalAppData%\[RANDOM CHARACTERS]Group: Malware file
%LocalAppData%\[RANDOM CHARACTERS].exe
File name: %LocalAppData%\[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%LocalAppData%\~[RANDOM CHARACTERS]
File name: %LocalAppData%\~[RANDOM CHARACTERS]Group: Malware file
%Temp%\smtmp\
File name: %Temp%\smtmp\Group: Malware file
%Temp%\smtmp\1
File name: %Temp%\smtmp\1Group: Malware file
%Temp%\smtmp\2
File name: %Temp%\smtmp\2Group: Malware file
%Temp%\smtmp\3
File name: %Temp%\smtmp\3Group: Malware file
%Temp%\smtmp\4
File name: %Temp%\smtmp\4Group: Malware file
%StartMenu%\Programs\System Recovery\
File name: %StartMenu%\Programs\System Recovery\Group: Malware file
%StartMenu%\Programs\System Recovery\System Recovery.lnk
File name: %StartMenu%\Programs\System Recovery\System Recovery.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%StartMenu%\Programs\System Recovery\Uninstall System Recovery.lnk
File name: %StartMenu%\Programs\System Recovery\Uninstall System Recovery.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%UserProfile%\Desktop\System Recovery.lnk
File name: %UserProfile%\Desktop\System Recovery.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
Registry Modifications
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main "Use FormSuggest" = 'Yes'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnonBadCertRecving" = '0'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "CertificateRevocation" = '0'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations "LowRiskFileTypes" = '/{hq:/s's:/ogn:/uyu:/dyd:/c'u:/bnl:/ble:/sdf:/lrh:/iul:/iulm:/fhg:/clq:/kqf:/'wh:/lqf:/lqdf:/lnw:/lq2:/l2t:/v'w:/rbs:'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments "SaveZoneInformation" = '1'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\ActiveDesktop "NoChangingWallPaper" = '1'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = '1'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer "NoDesktop" = '1'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "DisableTaskMgr" = '1'HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download "CheckExeSignatures" = 'no'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedMRU "MRUList"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced "Hidden" = '0'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced "ShowSuperHidden" = '0'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\..{RunKeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[RANDOM CHARACTERS]"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[RANDOM CHARACTERS].exe"
Additional Information
| # | Message |
|---|---|
| 1 | Activation Reminder System Recovery Activation Advanced module activation required to fix detected errors and performance issues. Please purchase Advanced Module license to activate this software and enable all features. |
| 2 | Critical Error A critical error has occurred while indexing data stored on hard drive. System restart required. |
| 3 | Critical Error Hard Drive not found. Missing hard drive. |
| 4 | Critical Error Hard drive critical error. Run a system diagnostic utility to check your hard disk drive for errors. Windows can't find hard disk space. Hard drive error. |
| 5 | Critical Error RAM memory usage is critically high. RAM memory failure. |
| 6 | Critical Error Windows can't find hard disk space. Hard drive error |
| 7 | Critical Error! Damaged hard drive clusters detected. Private data is at risk. |
| 8 | Critical Error! Windows was unable to save all the data for the file \System32\496A8300. The data has been lost. This error may be caused by a failure of your computer hardware. |
| 9 | Critical Hard Disk Drive Error System Recovery detected a bad sector on your hard disk drive. This error may cause the following problems: - Data corruption and loss - Hard drive inaccessibility - System errors and failures |
| 10 | Fix Disk System Recovery Diagnostics will scan the system to identify performance problems. Start or Cancel |
| 11 | Hard Drive Failure The system has detected a problem with one or more installed IDE / SATA hard disks. It is recommended that you restart the system. |
| 12 | System Error An error occurred while reading system files. Run a system diagnostic utility to check your hard disk drive for errors. |
| 13 | System Recovery Diagnostics Windows detected a hard disk error. A problem with the hard drive sectors has been detected. It is recommended to download the following sertified software to fix the detected hard drive problems. Do you want to download recommended software? |
| 14 | System Restore The system has been restored after a critical error. Data integrity and hard drive integrity verification required. |
| 15 | Windows - No Disk Exception Processing Message 0x0000013 |
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.