Windows XP Recovery
Posted: May 13, 2011
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Ranking: | 14,501 |
|---|---|
| Threat Level: | 10/10 |
| Infected PCs: | 2,780 |
| First Seen: | October 16, 2012 |
|---|---|
| Last Seen: | March 1, 2025 |
| OS(es) Affected: | Windows |
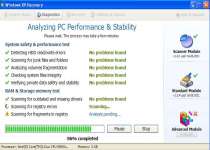 Windows XP Recovery is a rogue defragmenter (or 'defragger') that belongs to the FakeSysDef family and creates a wide range of different system warnings to give the appearance that your computer is heavily damaged. Although Windows XP Recovery strongly recommends that you purchase an activation key to cure these threats, the problems that Windows XP Recovery detects aren't real, and Windows XP Recovery itself has no threat detection or removal functions. You should delete Windows XP Recovery by using good anti-malware products, since some victims of Windows XP Recovery infections have reported that manually removing Windows XP Recovery resulted in other problems like impeded Internet connectivity.
Windows XP Recovery is a rogue defragmenter (or 'defragger') that belongs to the FakeSysDef family and creates a wide range of different system warnings to give the appearance that your computer is heavily damaged. Although Windows XP Recovery strongly recommends that you purchase an activation key to cure these threats, the problems that Windows XP Recovery detects aren't real, and Windows XP Recovery itself has no threat detection or removal functions. You should delete Windows XP Recovery by using good anti-malware products, since some victims of Windows XP Recovery infections have reported that manually removing Windows XP Recovery resulted in other problems like impeded Internet connectivity.
Windows XP Recovery: Not the First Rogue Defragger to Use the Windows Work Catalyst's Interface
Although Windows XP Recovery's name may be relatively new, Windows XP Recovery's code and functions are not – in fact, you can find many other clones of Windows XP Recovery that maul your computer's performance and security in the same ways. Some known clones of Windows XP Recovery include System Defragmenter, Ultra Defragger, HDD Control, Win HDD, Win Defrag, Disk Doctor, Hard Drive Diagnostic, HDD Diagnostic, HDD Plus, HDD Repair, HDD Rescue, Smart HDD, Defragmenter, HDD Tools, Disk Repair, Windows Optimization Center, Scanner, HDD Low, Hdd Fix and Win Defragmenter.
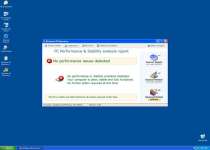
Windows XP Recovery supposedly offers a wide range of diverse functions that can clean up your system and protect your data, but these services are all cheap imitations. Any attempts to use your computer while Windows XP Recovery is active will result in being drowned out by a deluge of messages like these:
Low Disk Space
You are running very low disk space on Local Disk (C:).
System Restore
The system has been restored after a critical error. Data integrity and hard drive integrity verification required.
Activation Reminder
Windows Recovery Activation
Advanced module activation required to fix detected errors and performance issues. Please purchase Advanced Module license to activate this software and enable all features.
Windows - No Disk
Exception Processing Message 0x0000013
Critical Error
Hard Drive not found. Missing hard drive.
Critical Error
Windows can't find hard disk space. Hard drive error
Critical Error!
Damaged hard drive clusters detected. Private data is at risk.
Critical Error
RAM memory usage is critically high. RAM memory failure.
Critical Error
A critical error has occurred while indexing data stored on hard drive. System restart required.
Critical Error!
Windows was unable to save all the data for the file \System32\496A8300. The data has been lost. This error may be caused by a failure of your computer hardware.
Attempting to use any of the scanning functions that Windows Recovery offers you in bad faith will result in just more errors. Some commonly-reported scanner errors include:
Requested registry access is not allowed. Registry defragmentation required
32% of HDD space is unreadable
Registry Error - Critical Error
Drive C initializing error
Bad sectors on hard drive or damaged file allocation table
GPU RAM temperature is critically high. Urgent RAM memory optimization is required to prevent system crash
Hard drive doesn't respond to system commands
Ram Temperature is 83 C. Optimization is required for normal operation.
Read time of hard drive clusters less than 500 ms
Data Safety Problem. System integrity is at risk.
Besides being highly unlikely, these error messages are fake and contain no information worth acting on to fix your PC. Any problems you may experience with your computer are really the result of Windows XP Recovery or a related infection.
It goes without saying that purchasing a registration key for Windows XP Recovery is a pure waste of your money. If you give your credit card information to the criminal 'company' that promotes Windows XP Recovery, you should immediately talk to your credit card company and get all charges revoked.
The Unfriendly Friends That Windows XP Recovery Brings with It
Regrettably, even Windows XP Recovery isn't the only problem you may need to defeat. Threats in the Windows XP Recovery subgroup are often accompanied by TDSS rootkits that can infect preexisting processes to hide their own operations. These particular rootkits have earned a reputation for creating loud audio-based advertisements and hijacking web browsers. The latter attack may cause your web browser to redirect itself to a dangerous website or show fake warning screens.
Manually detecting and removing Windows XP Recovery and Windows XP Recovery's rootkits is tedious and difficult even for experts, which is why it's suggested that you instead use an anti-malware program to do so. By using Safe Mode, a non-Windows operating system boot, or a boot from a CD or other storage device, you can easily avoid Windows XP Recovery's Registry-based startup routine.
Avoiding the startup for the TDSS rootkit that came with Windows XP Recovery may be more difficult. If you experience problems in downloading or running anti-malware program files, even while you're in Safe Mode, try renaming the file. The names 'explorer.exe' and 'iexplore.exe' are often allowed by default by malware filter lists.
File System Modifications
- The following files were created in the system:
# File Name 1 %AllUsersProfile%\ .dll 2 %AllUsersProfile%\ .exe 3 %AllUsersProfile%\Application Data\.dll 4 %AllUsersProfile%\Application Data\.exe 5 %AllUsersProfile%\Application Data\~ 6 %AllUsersProfile%\Application Data\~r 7 %AllUsersProfile%\~ 8 %AllUsersProfile%\~ r 9 %Desktop%\Windows XP Recovery.lnk 10 %Programs%\Windows XP Recovery 11 %Programs%\Windows XP Recovery\Windows XP Recovery.lnk 12 %TempDir%\[RANDOM CHARACTERS] 13 %TempDir%\[RANDOM CHARACTERS].exe 14 %TempDir%\dfrg 15 %TempDir%\dfrgr 16 %UserProfile%\Desktop\Windows Recovery.lnk 17 %UserProfile%\Start Menu\Programs\Windows Recovery\ 18 %UserProfile%\Start Menu\Programs\Windows Recovery\Uninstall Windows Recovery.lnk 19 %UserProfile%\Start Menu\Programs\Windows Recovery\Windows Recovery.lnk
Registry Modifications
- The following newly produced Registry Values are:
HKEY..\..\..\..{Subkeys}HKCU\Software\Microsoft\Windows\CurrentVersion\Run "[RANDOM CAHARCETRS]"HKCU\Software\Microsoft\Windows\CurrentVersion\Run "[RANDOM CHARACTERS].exe"
Use SpyHunter to Detect and Remove PC Threats
If you are concerned that malware or PC threats similar to Windows XP Recovery may have infected your computer, we recommend you start an in-depth system scan with SpyHunter. SpyHunter is an advanced malware protection and remediation application that offers subscribers a comprehensive method for protecting PCs from malware, in addition to providing one-on-one technical support service.
* See Free Trial offer below. EULA and Privacy/Cookie Policy.
Why can't I open any program including SpyHunter? You may have a malware file running in memory that kills any programs that you try to launch on your PC. Tip: Download SpyHunter from a clean computer, copy it to a USB thumb drive, DVD or CD, then install it on the infected PC and run SpyHunter's malware scanner.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:C:\Documents and Settings\<username>\Documenti\Download\***s Rogue Pack\***'s Rogue Pack\DUMP_04E70000-04F69000.exe
File name: DUMP_04E70000-04F69000.exeSize: 1.01 MB (1019904 bytes)
MD5: dae81e01d143caaa70b126dc75971e58
Detection count: 30
File type: Executable File
Mime Type: unknown/exe
Path: C:\Documents and Settings\<username>\Documenti\Download\***s Rogue Pack\***'s Rogue Pack\DUMP_04E70000-04F69000.exe
Group: Malware file
Last Updated: April 6, 2024
Registry Modifications
File name without pathFile_Restore.lnk
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.