Windows Maintenance Suite
Posted: June 6, 2012
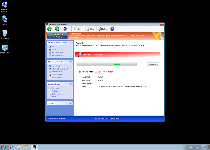
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
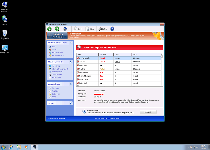
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 9 |
| First Seen: | June 6, 2012 |
|---|---|
| Last Seen: | January 8, 2020 |
| OS(es) Affected: | Windows |
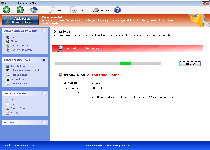 Windows Maintenance Suite, rather than being the all-in-one security suite that Windows Maintenance Suite claims to be, is a scamware product that displays inaccurate alerts about malware and other PC threats without even a cursory attempt at verifying the validity of its warnings. SpywareRemove.com malware experts have also traced Windows Maintenance Suite's lineage back to identical members of FakeVimes, a group of fake anti-malware scanners that are well-known for causing search engine redirects and attacking legitimate security programs. While Windows Maintenance Suite may be limited to attacking Windows, all modern versions of Windows should be considered at risk for a Windows Maintenance Suite infection, which should be removed by qualified security software whenever manageable.
Windows Maintenance Suite, rather than being the all-in-one security suite that Windows Maintenance Suite claims to be, is a scamware product that displays inaccurate alerts about malware and other PC threats without even a cursory attempt at verifying the validity of its warnings. SpywareRemove.com malware experts have also traced Windows Maintenance Suite's lineage back to identical members of FakeVimes, a group of fake anti-malware scanners that are well-known for causing search engine redirects and attacking legitimate security programs. While Windows Maintenance Suite may be limited to attacking Windows, all modern versions of Windows should be considered at risk for a Windows Maintenance Suite infection, which should be removed by qualified security software whenever manageable.
Why Maintaining a Safe Distance from Windows Maintenance Suite is What's Best for Your PC
Windows Maintenance Suite acts and looks like an anti-malware scanner in the most superficial terms possible, but as far as actual security features go, Windows Maintenance Suite's contributions are wholly negative. Windows Maintenance Suite is an active danger to your computer rather than helpful software. Symptoms of Windows Maintenance Suite's attacks that SpywareRemove.com malware researchers are familiarized with include:
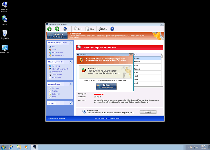
- Inaccurate pop-up alerts about malicious software or attacks against your PC. Alerts may be used to imply the presence of specific types of PC threat, as in the following example:
Warning! Virus Detected
Threat detected: FTP Server
Infected file: C:\Windows\System32\dllcache\wmpshell.dllAlternately, alerts may simply warn you about a nonexistent attack without specifying the software that's supposedly behind it, as in the contrasting example shown here:
Warning! Identity theft attempt detected
Hidden connection IP: 128.154.26.11
Target: Microsoft Corporation keys - Blocked applications that Windows Maintenance Suite pretends are infected or damaged in some way. These applications may be blocked at memory-level (by shutting down memory processes as Windows Maintenance Suite identifies them) or sabotaged (by removing relevant Registry entries) to prevent them from functioning at all. Programs that Windows Maintenance Suite may block include firewall utilities, anti-virus scanners, Task Manager and other Windows security tools.
- You may also be attacked by online search redirects that expose you to unusual or hostile sites, especially sites that serve as spam-based search engines. Windows Maintenance Suite's search redirects use a method that lets them function in all types of web browsers.
Blocking the Second Half of Windows Maintenance Suite's Two-Part Hoax
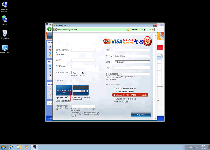
Windows Maintenance Suite's primary mission on your PC is to bamboozle you into paying for its registration key – all while pretending that doing so will grant you access to a new level of Windows Maintenance Suite-based protection that can remove all of its fake PC threats. Since SpywareRemove.com malware researchers have emphasized Windows Maintenance Suite's utter inability to deal with any type of real PC threat, you should never feel as though you need to spend money on Windows Maintenance Suite or any other member of Win32/FakeVimes such as Privacy Guard Pro, PrivacyGuard Pro 2.0, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus and Smart Security.
Because Windows Maintenance Suite has a high chance of interfering with deletion efforts, SpywareRemove.com malware experts additionally recommend booting your PC from a removable media device or using Safe Mode. Both of these options are simple ways to disable Windows Maintenance Suite's Registry-based startup routine. Either method will allow you to remove Windows Maintenance Suite without much trouble, provided you have access to even minimally competent anti-malware software.

Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%APPDATA%\Protector-hhjq.exe
File name: Protector-hhjq.exeSize: 1.97 MB (1970688 bytes)
MD5: 61bd519e9e84ea12d9af329d08be1f7a
Detection count: 20
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: January 8, 2020
%AppData%\NPSWF32.dll
File name: %AppData%\NPSWF32.dllFile type: Dynamic link library
Mime Type: unknown/dll
Group: Malware file
%AppData%\Protector-[RANDOM CHARACTERS].exe
File name: %AppData%\Protector-[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AppData%\result.db
File name: %AppData%\result.dbMime Type: unknown/db
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = "2012-2-17_2"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "rudbxijemb"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorAdmin" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorUser" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableLUA" = 0HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\ASProtectHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tapinstall.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\zapsetup3001.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ashDisp.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mostat.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\platin.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\divx.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\_avpcc.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\_avp32.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\..{RunKeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"
Additional Information
| # | Message |
|---|---|
| 1 | Error
Keylogger activity detected. System information security is at risk. It is recommended to activate protection and run a full system scan. |
| 2 | Error
Software without a digital signature detected. Your system files are at risk. We strongly advise you to activate your protection. |
| 3 | Error Keylogger activity detected. System information security is at risk. It is recommended to activate protection and run a full system scan. |
| 4 | Error Software without a digital signature detected. Your system files are at risk. We strongly advise you to activate your protection. |
we have been trying to remove windows maintenance for nearly 4 to 5 hours. it is becoming a really big deal, i have been completely locked out of all my programs and cannot access my task manager. I have had this computer since September 2011 and haven’t had not one single problem out of it and now all of a sudden I cant access my computer at all. This problem needs to be resolved as SOON as possible or I will notify the proper authorities including the FCC. Thank you…