Windows Pro Defence Kit
Posted: March 18, 2014
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 12 |
| First Seen: | March 18, 2014 |
|---|---|
| Last Seen: | January 8, 2020 |
| OS(es) Affected: | Windows |
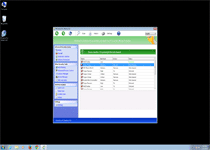
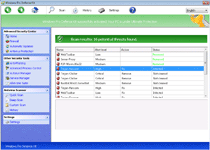
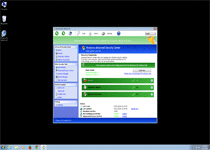
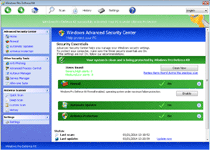
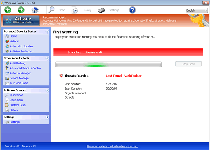 Windows Pro Defence Kit is a new clone of old, rogue anti-malware products that claim to offer your PC security services, when their real functions involve displaying fake information, attempting to defraud you of money and blocking most legitimate programs that could help your PC. Connected to infamous families like Tritax and FakePAV and belonging to the FakeVimes family, Windows Pro Defence Kit is just as much a danger to you as previous members of these scamware groups, and malware experts always urge you to remove Windows Pro Defence Kit as fast as possible. The use of additional security procedures usually will be needed before you can use any anti-malware utilities that can isolate and uninstall Windows Pro Defence Kit safely.
Windows Pro Defence Kit is a new clone of old, rogue anti-malware products that claim to offer your PC security services, when their real functions involve displaying fake information, attempting to defraud you of money and blocking most legitimate programs that could help your PC. Connected to infamous families like Tritax and FakePAV and belonging to the FakeVimes family, Windows Pro Defence Kit is just as much a danger to you as previous members of these scamware groups, and malware experts always urge you to remove Windows Pro Defence Kit as fast as possible. The use of additional security procedures usually will be needed before you can use any anti-malware utilities that can isolate and uninstall Windows Pro Defence Kit safely.
The Defence Kit that's Plundering Your Wallet
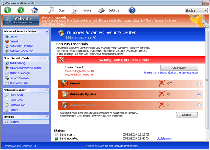
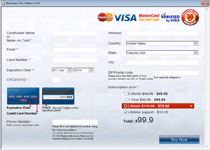
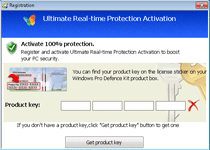
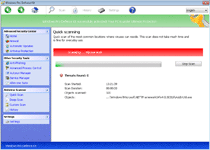
Windows Pro Defence Kit is another update given to previous, equally fake anti-malware products that pretend to scan your PC for threats – only to, inevitably, find new infections continuously. While Windows Pro Defence Kit doesn't detect real threat, Windows Pro Defence Kit is capable of pulling up lists of legitimate threat names in its fraudulent system scanner results. More significantly than that, malware researchers also have connected Windows Pro Defence Kit's fraudulent security functions with attacks that can block unrelated applications.
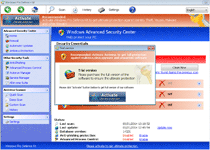
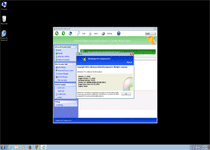
The latter usually will trigger for security-related products, such as Task Manager or major anti-virus brands. Windows Pro Defence Kit also can prevent you from using some brands of Web browsers or instant messaging programs. Whatever its target might be, Windows Pro Defence Kit's attack will display a fake firewall alert that implies that the associated program has been compromised by threats with network communication capabilities. When paying Windows Pro Defence Kit its requested fee, Windows Pro Defence Kit will pretend to remove this threat from your computer, which malware experts naturally don't recommend, since Windows Pro Defence Kit wastes money, in exchange for no real security features at all.
Taking the Professional Recourse to Windows Pro Defence Kit's Attacks
Windows Pro Defence Kit is no more of a net advantage to your PC's security than any Trojan would be, and malware researchers find its removal to be essential for your PC's safety and privacy. Because of its habit of terminating other programs, you often will find it necessary to disable Windows Pro Defence Kit before Windows Pro Defence Kit can be uninstalled. Safe Mode combined with common backup OS devices, such as USB drives, will give you the perfect environment for doing so. With Windows Pro Defence Kit disabled, thorough anti-malware scans should be used for removing Windows Pro Defence Kit and for making sure that no other threatening software has compromised your PC. Most scamware products like Windows Pro Defence Kit benefit from the attacks of related PC threats, such as Trojan downloaders.
Distribution methods for Windows Pro Defence Kit may encompass fake software updates, fraudulent online scanners and mislabeled spam attachments, many of which may be traced to corrupted websites or links. Strong browser security is an essential step in blocking potential installation methods for Windows Pro Defence Kit, which is more difficult to remove than Windows Pro Defence Kit is to detect and delete before Windows Pro Defence Kit's installed. Similar precautions are just as relevant to clones of Windows Pro Defence Kit, which malware experts have examined under diverse names such as Privacy Guard Pro, PrivacyGuard Pro 2.0, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus and Smart Security.

Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:svc-qtgs.exe
File name: svc-qtgs.exeSize: 1.22 MB (1226240 bytes)
MD5: a9a08bef52b281d00861201fa8ec132b
Detection count: 27
File type: Executable File
Mime Type: unknown/exe
Group: Malware file
Last Updated: January 8, 2020
Registry Modifications
HKEY..\..\{Value}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "S_SC" = %AppData%\svc-[RANDOM CHARACTERS].exeHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "ZSFT" = %AppData%\svc-[RANDOM CHARACTERS].exeHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "MS-SEC" = %AppData%\svc-[RANDOM CHARACTERS].exeHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "SD-986-001" = %AppData%\svc-[RANDOM CHARACTERS].exeHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations "LowRiskFileTypes" = ".zip;.rar;.nfo;.txt;.exe;.bat;.com;.cmd;.reg;.msi;.htm;.html;.gif;.bmp;.jpg;.avi;.mpg;.mpeg;.mov;.mp3;.m3u;.wav;"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments "SaveZoneInformation" = 1HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon "Shell" = "%AppData%\svc-[RANDOM CHARACTERS].exe"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorAdmin" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorUser" = 0HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\bckd "ImagePath" = 22.sys HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableLUA" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableVirtualization" = 0HKEY..\..\..\..{Subkeys}HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exeHKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exeHKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\MSASCui.exeHKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\msconfig.exeHKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpCmdRun.exeHKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpUXSrv.exeHKEY_LOCAL_MACHINE\Software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\k9filter.exe
Additional Information
| # | Message |
|---|---|
| 1 | Error Potential malware detected. It is recommended to activate the protection and perform a thorough system scan to remove the malware. |
| 2 | Error Software without a digital signature detected. Your system files are at risk. We strongly advise you to activate your protection. |
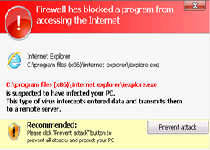
| 3 | Firewall has blocked a program from accessing the Internet Malwarebytes' Anti-Malware C:\program files\malwarebytes' anti-malware\mbam.exe C:\program files\malwarebytes' anti-malware\mbam.exe is suspected to have infected your PC. This type of virus intercepts entered data and transmits them to a remote server. |
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.