Windows Functionality Checker
Posted: February 17, 2012
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 28 |
| First Seen: | February 17, 2012 |
|---|---|
| Last Seen: | May 6, 2024 |
| OS(es) Affected: | Windows |
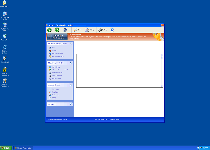
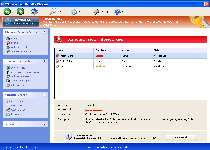 Windows Functionality Checker is a fake anti-malware and security scanner from the Rogue:Win32/FakePAV subgroup of scamware. Going by looks alone, Windows Functionality Checker appears to be able to detect malicious software and bears a strong resemblance to Microsoft Security Essentials, but Windows Functionality Checker completely avoids any attempt to find or remove actual PC threats from your computer. Repeated alerts and fake scans from Windows Functionality Checker are only used to bludgeon you into spending money on Windows Functionality Checker's fake 'full version,' and SpywareRemove.com malware experts warn that Windows Functionality Checker may even monitor and attempt to close other programs, including security applications. Since Windows Functionality Checker is a security risk, as well as a fraudulent overall product, it's suggested that you remove Windows Functionality Checker with a real anti-malware scanner whenever the chance is available.
Windows Functionality Checker is a fake anti-malware and security scanner from the Rogue:Win32/FakePAV subgroup of scamware. Going by looks alone, Windows Functionality Checker appears to be able to detect malicious software and bears a strong resemblance to Microsoft Security Essentials, but Windows Functionality Checker completely avoids any attempt to find or remove actual PC threats from your computer. Repeated alerts and fake scans from Windows Functionality Checker are only used to bludgeon you into spending money on Windows Functionality Checker's fake 'full version,' and SpywareRemove.com malware experts warn that Windows Functionality Checker may even monitor and attempt to close other programs, including security applications. Since Windows Functionality Checker is a security risk, as well as a fraudulent overall product, it's suggested that you remove Windows Functionality Checker with a real anti-malware scanner whenever the chance is available.
The Hidden Functions That Wait Underneath Windows Functionality Checker's Fake Features
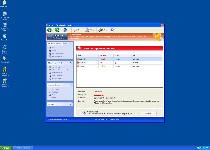
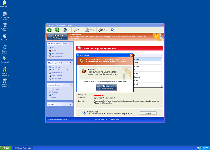
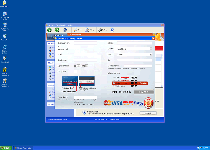
Windows Functionality Checker does its best to appear as trustworthy as Microsoft Security Essentials, and to this end, copies a great deal of the latter's appearance. Functions that Windows Functionality Checker pretends to possess can include complete system scans for malicious software, automatic self-updating and protection against phishing attacks. However, all of Windows Functionality Checker's features are fake and only imitate the appearance of being useful while avoiding any actual payoff that would benefit your PC. SpywareRemove.com malware experts especially emphasize that Windows Functionality Checker can neither find nor delete PC threats, such as worms, Trojans or rootkits from your computer. However, Windows Functionality Checker may use warning messages like the ones below to fool you into thinking differently:
Warning!
Location: [application file path]
Viruses: Backdoor.Win32.Rbot
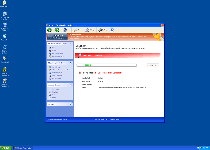
Warning! Database update failed!
Database update failed!
Outdated viruses databases are not effective and can`t [sic] guarantee adequate protection and security for your PC!
Click here to get the full version of the product and update the database!
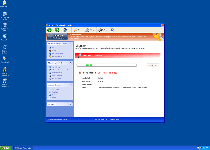
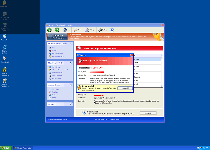
Warning! Running trial version!
The security of your computer has been compromised!
Now running trial version of the software!
Click here to purchase the full version of the software and get full protection for your PC!
Windows Functionality Checker may also attempt to scan your memory and close programs that Windows Functionality Checker judges as undesirable – such as anti-malware products that could remove Windows Functionality Checker from your computer. Other targets can include Adobe-brand software, webcam tools, downloading utilities, instant messengers, certain brands of web browsers and script packages like JavaScript. Since Windows Functionality Checker may shut down the anti-malware programs that could detect and remove Windows Functionality Checker safely, SpywareRemove.com malware analysts recommend disabling Windows Functionality Checker before trying to scan your PC. To achieve this, boot into Safe Mode, which is available on all Windows computers.
Where an Extensive Check Up on Windows Functionality Checker Leads You
Windows Functionality Checker was only noted as a danger in February of 2012, but Windows Functionality Checker's family of scamware is significantly older than this date and extends back to 2011. Similar programs from Windows Functionality Checker's classification include, for just a few examples, Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0. You should treat all of these members of the FakeVimes family of rogue security products to be just as hostile to your PC as Windows Functionality Checker would be and remove them with a similar application of anti-malware software.
Detecting Windows Functionality Checker in the first place should prove simple even for non-experts in PC security, since Windows Functionality Checker will launch itself automatically and may display simulated scans or warning pop-ups that should be easily-identified. However, SpywareRemove.com malware research team warns against using any included uninstall feature that Windows Functionality Checker may appear to possess, since included removal utilities will rarely, if ever, delete the entirety of a rogue security program like Windows Functionality Checker.
Aliases
Use SpyHunter to Detect and Remove PC Threats
If you are concerned that malware or PC threats similar to Windows Functionality Checker may have infected your computer, we recommend you start an in-depth system scan with SpyHunter. SpyHunter is an advanced malware protection and remediation application that offers subscribers a comprehensive method for protecting PCs from malware, in addition to providing one-on-one technical support service.
* See Free Trial offer below. EULA and Privacy/Cookie Policy.
Why can't I open any program including SpyHunter? You may have a malware file running in memory that kills any programs that you try to launch on your PC. Tip: Download SpyHunter from a clean computer, copy it to a USB thumb drive, DVD or CD, then install it on the infected PC and run SpyHunter's malware scanner.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%APPDATA%\Protector-gqm.exe
File name: Protector-gqm.exeSize: 1.99 MB (1994752 bytes)
MD5: 9874377f3464e692bf0ccf043149639a
Detection count: 38
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: February 20, 2012
%APPDATA%\Protector-bth.exe
File name: Protector-bth.exeSize: 1.99 MB (1993728 bytes)
MD5: 19faf3d1d044bffd46a220a928d4ac00
Detection count: 34
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: February 20, 2012
%APPDATA%\Protector-okv.exe
File name: Protector-okv.exeSize: 1.99 MB (1996288 bytes)
MD5: f8c41a6dcfb38a3cb28a74ba5a8430b0
Detection count: 27
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: February 20, 2012
C:\rogueware samples\WintionalityChecker samples\Protector-wrm.exe
File name: Protector-wrm.exeSize: 1.99 MB (1996288 bytes)
MD5: c6200cf2220feb8fef9e2112496d1378
Detection count: 9
File type: Executable File
Mime Type: unknown/exe
Path: C:\rogueware samples\WintionalityChecker samples\Protector-wrm.exe
Group: Malware file
Last Updated: May 6, 2024
%APPDATA%\Protector-pma.exe
File name: Protector-pma.exeSize: 1.99 MB (1994240 bytes)
MD5: f049dfdbecd316dd36d970cb9568cb8c
Detection count: 7
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: February 20, 2012
%AppData%\NPSWF32.dll
File name: %AppData%\NPSWF32.dllFile type: Dynamic link library
Mime Type: unknown/dll
Group: Malware file
%AppData%\Protector-oak.exe
File name: %AppData%\Protector-oak.exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%CommonPrograms%\Windows\Functionality Checker.lnk
File name: %CommonPrograms%\Windows\Functionality Checker.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%DesktopDir%\Windows\Functionality Checker.lnk
File name: %DesktopDir%\Windows\Functionality Checker.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
Registry Modifications
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run!Inspector
Father in law called me up in a panic cause thing thing had ienatllsd itself.. luckily he hadnt paid for it DO nto wait around this thing is evil.. Kill it asap. I did a system restore to 10 days ago and then found the files and manaully deleted.. It really will not let you do anything while it runs (including task manager)