Internet Security
Posted: February 2, 2012
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Ranking: | 19,194 |
|---|---|
| Threat Level: | 10/10 |
| Infected PCs: | 2,902 |
| First Seen: | February 2, 2012 |
|---|---|
| Last Seen: | February 8, 2025 |
| OS(es) Affected: | Windows |
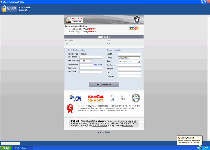
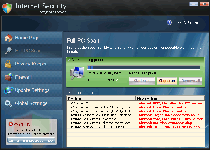 Internet Security is a member of the FakeRean family of fake anti-malware programs. According to its pop-up alerts and scanner simulations, Internet Security pretends to offer protection from spyware and other types of PC threats, but SpywareRemove.com malware researchers emphasize Internet Security's complete inability to find or remove any sort of actual and malicious software. Like other members of its family, Internet Security will launch itself without permission and may do so repeatedly whenever you try to open an executable file to prevent you from disabling Internet Security and facilitating its removal with anti-malware software. Like most forms of fake security programs, Internet Security's foremost goal is to gain access to your credit card information and linked finances, and it's recommended that you never purchase Internet Security, even as a step to assist with its total deletion.
Internet Security is a member of the FakeRean family of fake anti-malware programs. According to its pop-up alerts and scanner simulations, Internet Security pretends to offer protection from spyware and other types of PC threats, but SpywareRemove.com malware researchers emphasize Internet Security's complete inability to find or remove any sort of actual and malicious software. Like other members of its family, Internet Security will launch itself without permission and may do so repeatedly whenever you try to open an executable file to prevent you from disabling Internet Security and facilitating its removal with anti-malware software. Like most forms of fake security programs, Internet Security's foremost goal is to gain access to your credit card information and linked finances, and it's recommended that you never purchase Internet Security, even as a step to assist with its total deletion.
Internet Security: Hollow Security Software That's Wallpapered with Lies
Internet Security does have the basic appearance of a seemingly functional type of anti-malware scanner, but Internet Security's looks are also a clear giveaway to its true intentions, since Internet Security is visually identical to other clones from the FakeRean family such as Antivirus 2008 Pro, Windows Antivirus 2008, Vista Antivirus 2008, Antivirus XP 2008, PC Clean Pro, Antivirus Pro 2009, AntiSpy Safeguard, ThinkPoint, Spyware Protection 2010, Internet Antivirus 2011, Palladium Pro, XP Anti-Virus 2011, CleanThis, Rogue.Vista Antivirus 2008, XP Home Security 2012, XP Security 2012 and AntiVirus PRO 2015. SpywareRemove.com malware experts recommend that you completely disregard scanner results, taskbar notifications, pop-up alerts and other forms of fake information that Internet Security may try to feed you; this can even include falsified warnings about problems with specific applications.
Other characteristics by which Internet Security can be identified include:
- Browser-hijacking redirects that take you away from security websites or towards sites that promote Internet Security. This can also include modified browser settings such as a changed homepage.
- A fake Security Center applet that replaces the real Windows Security Center with a non-functional display – other than its ability to link you to hostile websites.
- Automatic startup behavior by Internet Security, which will, once launched, attempt to resist being closed by normal methods – even if Internet Security has to run as a background process to do so.
Ripping Down Internet Security's Self-Serving Propaganda
Although Internet Security may include a fake or poorly functional removal tool, SpywareRemove.com malware research team recommends the usage of a real anti-malware program to be certain of removing all of Internet Security's components. If Internet Security appears to block your software, you may need to use additional measures, such as booting into Safe Mode (which can be accessed by tapping F8 before Windows starts to load) to insure that Internet Security is unable to stop your system scans.
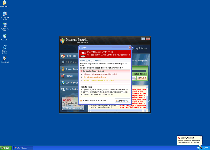
Along with its characteristic attacks, you may also be able to detect Internet Security or one of its clones by watching for similar types of unlikely and alarming system alerts. These fraudulent alerts can be recognized by the following text:
"Spyware alarm!
Our scan has reported that pieces of malicious spyware code are present on your hard drive. To get rid of security threats, click here for a [Rogue security program name] scan."
"Windows Security Center reports that Internet Security is enable. Internet Security helps to protect your computer against viruses and other security threats. Click Recommendations for the suggested actions. Your system might be at risk now.
Note: Windows has detected an unregistered version of '[Rogue security program name]'"
"Trojan detected!
A piece of malicious code was found in your system which can replicate itself if no action is taken. Clicked here to have your system cleaned by Internet Security."
"WARNING! Internet Security has found [random number] useless and UNWANTED files on your computer!"


Use SpyHunter to Detect and Remove PC Threats
If you are concerned that malware or PC threats similar to Internet Security may have infected your computer, we recommend you start an in-depth system scan with SpyHunter. SpyHunter is an advanced malware protection and remediation application that offers subscribers a comprehensive method for protecting PCs from malware, in addition to providing one-on-one technical support service.
* See Free Trial offer below. EULA and Privacy/Cookie Policy.
Why can't I open any program including SpyHunter? You may have a malware file running in memory that kills any programs that you try to launch on your PC. Tip: Download SpyHunter from a clean computer, copy it to a USB thumb drive, DVD or CD, then install it on the infected PC and run SpyHunter's malware scanner.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%AppData%\isecurity.exe
File name: isecurity.exeSize: 841.72 KB (841728 bytes)
MD5: 1cb245d7034fb2f6ad470b3464cd4080
Detection count: 73
File type: Executable File
Mime Type: unknown/exe
Path: %AppData%
Group: Malware file
Last Updated: August 17, 2022
%appdata%\isecurity.exe
File name: %appdata%\isecurity.exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Registry Modifications
File name without pathInternet Security.lnkRegexp file mask%AppData%\isecurity.exeHKEY..\..\..\..{Subkeys}HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\Internet Security
Related Posts
- Dr. Wolf Internet Security
- 'Internet Security Alert! Code: 055BCCAC9FEC' Pop-Ups
- 'Warning: Internet Security Damaged!' Pop-Up
- Avlab Internet Security XP/Vista/Win 7/Win 8 Antivirus 2015
- Internet Security Protection
yes, today Internet Security is a big problem. We should more cpncern about that. Thanks author for sharing this.
This has happened to me today, i think I pressed something and it popped up. How do I get rid of Internet Security??
Finally something to remove Internet Security! Holy SHI* I wasted 2 hours of my life searching around. You guys rock!
it blocks internet explorer and chrome so cant download and cant find any files of it help?
Security setting will not me open mail
I have read the first and second paragraph of this post and I realized that internet security actually cannot remove any spywares and adwares automatically. I auto starts and there is no way to stop it but the Norton Internet Security that I am using from 2009 is providing good security in my computer and my PC is never got any malware problem till I am using it. I have posted a big review about NIS 2014 that you can read on
But another thing I know is spywares and malwares can be removed on manual scan as Norton removes tracking cookies on manual quick scan...