WannaCryptor Ransomware (WanaCrypt0r Ransomware)
Posted: March 29, 2017
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 83 |
| First Seen: | March 29, 2017 |
|---|---|
| Last Seen: | November 15, 2019 |
| OS(es) Affected: | Windows |
The first major ransomware attack of 2017 involves the use of the WanaCrypt0r Ransomware, an improved version of the '.wcry File Extension' Ransomware which, unfortunately, leverages one of the leaked NSA exploits to exploit vulnerable computers running Windows XP. It is unknown which is the hacking group behind the WanaCrypt0r Ransomware attacks, but one thing is for certain – whoever they are, they certainly know what they are doing. The targets of the WanaCrypt0r Ransomware don't appear to b chosen randomly since most of the infected machines appear to belong to major companies in various industries around the world. However, the biggest victim of the WanaCrypt0r Ransomware appears to be Britain's National Healthcare Service (NHS), as many of the hospitals on the island have had their data locked by this file-encryption Trojan. Apart from the British NHS, the organization behind the WanaCrypt0r Ransomware also has attacked a large number of computers in Taiwan, Russia, Spain and Ukraine.
The initial infection with the WanaCrypt0r Ransomware usually occurs via spam emails that contain an infected attachment. Once the WanaCrypt0r Ransomware is deployed to a computer, it attempts to use the aforementioned NSA exploit named 'EternalBlue' to spread itself to other computers on the same network. The 'EternalBlue' exploit looks for an unpatched vulnerability in the SMB (Server Message Block) service and attempts to use it to spread to other computers on the same network. This worm-like behavior is very threatening as it has allowed the WanaCrypt0r Ransomware to take the medical records and data of entire hospitals as a hostage. It is important to mention that the 'EternalBlue' exploit only affects unpatched and insecure versions of all OSes between Windows XP and Windows 2012. Unfortunately, many hospitals and government institutions worldwide use outdated software, which gives the authors of the WanaCrypt0r Ransomware an opportunity to increase the damage their attacks can cause drastically.
The WanaCrypt0r Ransomware uses a secure encryption, and it is highly unlikely that we'll see a free decryptor anytime soon. When the file-encryption Trojan infiltrates a computer, it will proceed to encrypt data found there by using a combination of AES and RSA keys. Every locked file also will have its extension changed to '.WCRY' or '.WNCRYT.' The threat targets a total of 166 file extensions so that, unfortunately, its attacks are almost guaranteed to leave most files on computers in an encrypted state.
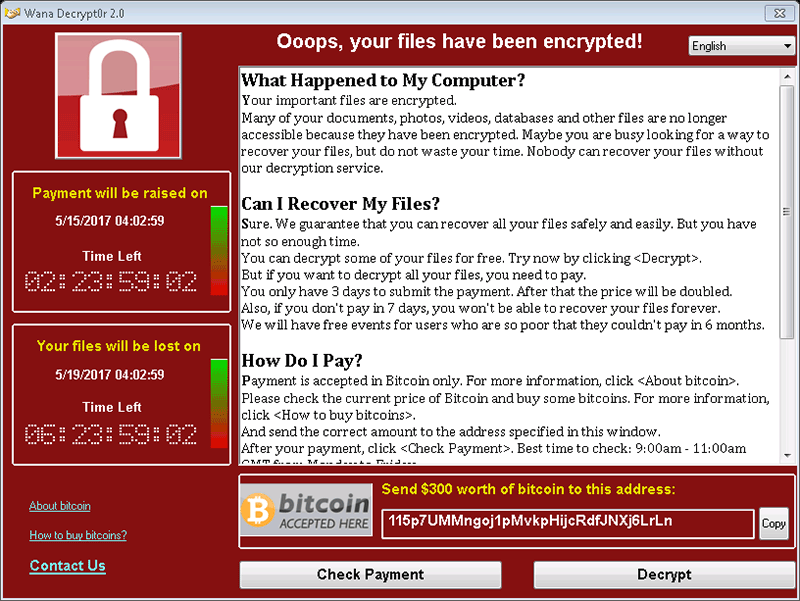
After the encryption routine is completed, the WanaCrypt0r Ransomware will proceed to display the ransom message which is stored in several files:
- @Please_Read_Me@.txt – for a text version of the ransom note.
- @WanaDecryptor@.bmp – image which contains a ransom message and is automatically set as the default Windows background.
- WanaDecryptor.exe – decryption utility which only works if the payment is made, and also contains a ransom message.
- @WanaDecryptor@.exe – an alternative file whose purpose is to acquire the 'WanaDecryptor.exe' file if the victim's antivirus software has removed it.
The ransom note containing more details is found by launching 'WanaDecryptor.exe.' This will spawn a new program window that contains a timer, the message, and buttons used to check the payment status and decrypt the files if the payment has been verified. The authors note that victims have a limited amount of time to pay the ransom sum or they'll suffer different consequences – first, the ransom sum will be increased, and later their decryption key will be deleted. It seems like the WanaCrypt0r Ransomware's ransom sum is fixed to $300 and, naturally, the authors want the money to be transferred via Bitcoins. The ransom note features translations to several languages - Bulgarian, Chinese (Simplified), Chinese (Traditional), Croatian, Czech, Danish, Dutch, English, Filipino, Finnish, French, German, Greek, Indonesian, Italian, Japanese, Korean, Latvian, Norwegian, Polish, Portuguese, Romanian, Russian, Slovak, Spanish, Swedish, Turkish, Vietnamese.
'What Happened to My Computer?
Your important files are encrypted.
Many of your documents, photos, videos, databases and other files are no longer accessible because they have been encrypted. Maybe you are busy looking for a way to recover your files, but do not waste your time. Nobody can recover your files without our decryption service.
Can I Recover My Files?
Sure. We guarantee that you can recover all your files safely and easily. But you have not so enough time.
You can decrypt some of your files for free. Try now by clicking .
But if you want to decrypt all your files, you need to pay.
You only have 3 days to submit the payment. After that the price will be doubled.
Also, if you don’t pay in 7 days, you won’t be able to recover your files forever.
We will have free events for users who are so poor that they couldn’t pay in 6 months.
How Do I Pay?
Payment is accepted in Bitcoin only. For more information, click .
Please check the current price of Bitcoin and buy some bitcoins. For more information, click .
And send the correct amount to the address specified in this window.
After your payment, click . Best time to check: 9:00am - 11:00am GMT from Monday to Friday.
Once the payment is checked, you can start decrypting your files immediately.
Contact
If you need our assistance, send a message by clicking .
We strongly recommend you to not remove this software, and disable your antivirus for a while, until you pay and the payment gets processed. If your anti-virus gets updated and removes this software automatically, it will not be able to recover your files even if you pay!'
The authors of the WanaCrypt0r Ransomware are probably aware how powerful their crypto-threat is, and that's why they've added several additional features to ensure that attacks will inflict the maximum amount of damage. When launched, the WanaCrypt0r Ransomware will execute several commands, which aim to terminate processes related to popular database servers. This way, the database files will not be locked, and the WanaCrypt0r Ransomware will be able to access and encrypt their contents. In addition to this, the WanaCrypt0r Ransomware will attempt to wipe the Shadow Volume Copies, but this might not always work successfully so that some victims might be able to recover from the attack partially via the Shadow Volume Copies.
Paying the ransom sum that the WanaCrypt0r Ransomware demands is not advised, because the money might be used to fund future projects of the hacking group, therefore making it more likely that you'll end up meeting another one of their sinister cyber threats. The best way to counter threats like the WanaCrypt0r Ransomware is to make sure that they never have a chance to get to your files. In the case of the WanaCrypt0r Ransomware, the best thing to do is to keep your anti-virus software active and updated, as well as to apply the latest security updates for your operating system.
Use SpyHunter to Detect and Remove PC Threats
If you are concerned that malware or PC threats similar to WannaCryptor Ransomware (WanaCrypt0r Ransomware) may have infected your computer, we recommend you start an in-depth system scan with SpyHunter. SpyHunter is an advanced malware protection and remediation application that offers subscribers a comprehensive method for protecting PCs from malware, in addition to providing one-on-one technical support service.
* See Free Trial offer below. EULA and Privacy/Cookie Policy.
Why can't I open any program including SpyHunter? You may have a malware file running in memory that kills any programs that you try to launch on your PC. Tip: Download SpyHunter from a clean computer, copy it to a USB thumb drive, DVD or CD, then install it on the infected PC and run SpyHunter's malware scanner.
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.