NameChanger
Posted: February 14, 2014
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 1/10 |
|---|---|
| Infected PCs: | 129 |
| First Seen: | February 14, 2014 |
|---|---|
| Last Seen: | June 17, 2023 |
| OS(es) Affected: | Windows |
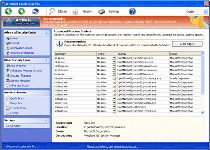 NameChanger is a general term for members of the Tritax family of fake anti-malware programs. By imitating the appearances of actual anti-malware products and delivering false system information about the presence of threats, NameChanger variants attempt to bully their victims into buying their software, which, supposedly, can remove all detected threats. Malware experts and others in the métier have seen a recent boom in the NameChanger-distributing campaign, which has targeted popular websites for both Americans and Europeans. The usual anti-malware tools and techniques continue to be recommended after any accidental installation of a NameChanger variant, which may use installation pop-ups reminiscent of the Microsoft software.
NameChanger is a general term for members of the Tritax family of fake anti-malware programs. By imitating the appearances of actual anti-malware products and delivering false system information about the presence of threats, NameChanger variants attempt to bully their victims into buying their software, which, supposedly, can remove all detected threats. Malware experts and others in the métier have seen a recent boom in the NameChanger-distributing campaign, which has targeted popular websites for both Americans and Europeans. The usual anti-malware tools and techniques continue to be recommended after any accidental installation of a NameChanger variant, which may use installation pop-ups reminiscent of the Microsoft software.
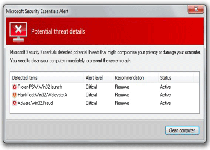
When 'Microsoft' Recommends Installing a Threat
NameChanger can refer to any of three currently-identified branches of the family of scamware: NameChanger.A, NameChanger.B and NameChanger.C. Each of these branches seeks to imitate the appearances of different brands of real PC security products; examples from all three branches include . However, malware researchers and others have verified that there are well over two hundred separate names for NameChanger – hence its name.
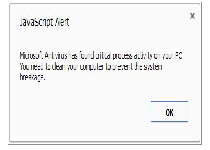
NameChanger's installers have been known to use everything from hacked advertising rings for legitimate instant messengers to hacked websites like DailyMotion.com. Typical attacks include the injection of browser-redirecting content that especially targets Internet Explorer users, forcing their exposure to a fake alert that claims to be part of the Microsoft Security Essentials. The update, of course, doesn't have any kind of real security software, but, instead, is a pathway for NameChanger to compromise your PC. In the process of doing so, NameChanger will display fake system-scanning results and a variety of fake pop-up alerts, all meant to make you buy its registration key.
By itself, the act of registering NameChanger is harmless, and you can feel free to do so with any freely-distributed keys from real PC security companies. However, malware researchers warn that giving information to NameChanger's fake company is nothing less than giving it over to the bad guys, who may use it to commit financial or identity-related fraud.
Changing Your Browsing Habits to Escape the NameChanger
Many of the most recent attacks for NameChanger have targeted Internet Explorer to the point of ignoring Chrome, Firefox and other browsers, which may remain safe from exposure to most NameChanger-installing pop-ups. Besides the simple solution of switching browsers, malware experts also suggest updating your software regularly, disabling scripts and having anti-malware products that include Web browser-protecting functions. When taken together, these forms of protection can provide the best defense against NameChanger, even when you're exposed to NameChanger from a site that should be safe.
PC users who aren't in danger of buying NameChanger still will have their own issues to deal with; removing NameChanger may be made difficult by its blocking of other programs necessary for disinfecting your PC. Blocking any given variant of NameChanger through such basic security techniques as Safe Mode, followed by removing NameChanger with real anti-malware software is the form of resolution encouraged by malware researchers.
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.