Win 7 Home Security 2012
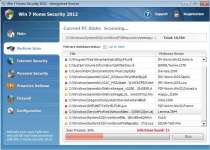 Win 7 Home Security 2012 is a repackaging of related threats like Vista Home Security 2011 and System Smart Security. Infections of Win 7 Home Security 2012 are known to block programs from running and hijack web browsers to control which websites you visit, in addition to creating fake anti-virus pop-up warnings. These attacks don't damage the operating system or programs themselves, and removing Win 7 Home Security 2012 with the proper application of security software will also cause the above problems to vanish.
Win 7 Home Security 2012 is a repackaging of related threats like Vista Home Security 2011 and System Smart Security. Infections of Win 7 Home Security 2012 are known to block programs from running and hijack web browsers to control which websites you visit, in addition to creating fake anti-virus pop-up warnings. These attacks don't damage the operating system or programs themselves, and removing Win 7 Home Security 2012 with the proper application of security software will also cause the above problems to vanish.
Win 7 Home Security 2012: A Year Early to the Party and Bringing Poisonous Presents
The majority of Win 7 Home Security 2012 infections are caused by Trojans that attack your computer by exploiting web browser security limitations, although you may also download Win 7 Home Security 2012 by mistake from a website with poor prerequisites for file uploads.
Like many other threats, Win 7 Home Security 2012 pretends to be an independent program, but Win 7 Anti-Spyware 2012 is really a copy of other recent rogue security programs. Examples of Win 7 Home Security 2012 relatives include Vista Home Security 2012, XP Home Security 2012, System Smart Security and Internet Security 2011.
Win 7 Home Security 2012 is known for the following high-level security attacks on any computer that Win 7 Anti-Spyware 2012 infects:
- Allows browser hijackers to take control of your web browser's destinations, creates fake content like inaccurate website errors, alters browser settings like your homepage and play advertisements. Win 7 Home Security 2012 hijacks don't damage your web browser, but will continue until you remove Win 7 Home Security 2012.
- Preventing you from using applications, sometimes with the use of error messages that make it look like the program is infected. Win 7 Home Security 2012 may continue to block these programs as long as Win 7 Anti-Spyware 2012 is active, and may remain active in the background as a hidden memory process.
Win 7 Home Security 2012's Further Pop-Up-Based Deceptions
Win 7 Home Security 2012's fake anti-virus and security features will also be present in the form of inaccurate system scans and fake infection pop-ups. Win 7 Home Security 2012's scans will always find fake infections, while Win 7 Home Security 2012's pop-ups will warn you about serious threats that aren't on your computer to begin with:
System warning!
Continue working in unprotected mode is very dangerous. Viruses can damage your confidential data and work on your computer. Click here to protect your computer.
System warning!
Security Essentials Ultimate Pack software detects programs that may compromise your privacy and harm your systems. It is highly recommended you scan your PC right now. Click here to start.
Security Alert!
Your computer is being attacked from a remote machine!
Block Internet access to your computer to prevent system infection.
Critical Warning!
Critical System Warning! Your system is probably infected with a version of Trojan-Spy.HTML.Visafraud.a. This may result in website access passwords being stolen from Internet Explorer, Mozilla Firefox, Outlook etc. Click Yes to scan and remove threats. (recommended)
Once you delete Win 7 Home Security 2012, all associated problems will likewise be removed. It's recommended that you only try to delete Win 7 Home Security 2012 by using high-quality security scanners; improperly removing Win 7 Home Security 2012 can let Win 7 Home Security 2012 return after a reboot or system restore.
For the highest chance of successfully removing Win 7 Home Security 2012, use your software in Safe Mode or boot your PC from an external storage device. These solutions will temporarily disable Win 7 Home Security 2012, so that you can continue with the removal attempt without any obstacles.
File System Modifications
- The following files were created in the system:
# File Name 1 %AllUsersProfile%\[random] 2 %AppData%\Local\[RANDOM CHARACTERS] 3 %AppData%\Local\[random].exe 4 %AppData%\Roaming\Microsoft\Windows\Templates\[RANDOM CHARACTERS] 5 %Temp%\[RANDOM CHARACTERS] 6 [RANDOM CHARACTERS].exe 7 Uninstall Win 7 Home Security 2012.lnk 8 Win 7 Home Security 2012.lnk
Registry Modifications
- The following newly produced Registry Values are:
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Classes\.exe “(Default)” = ‘exefile’HKEY_CURRENT_USER\Software\Classes\.exe “Content Type” = ‘application/x-msdownload’HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon “(Default)” = ‘%1? = ‘”%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe” /START “%1? %*’HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command “IsolatedCommand” = ‘”%1? %*’HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command “(Default)” = ‘”%1? %*’HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command “IsolatedCommand” = ‘”%1? %*’HKEY_CURRENT_USER\Software\Classes\exefile “(Default)” = ‘Application’HKEY_CURRENT_USER\Software\Classes\exefile “Content Type” = ‘application/x-msdownload’HKEY_CURRENT_USER\Software\Classes\exefile\DefaultIcon “(Default)” = ‘%1?HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe” /START “%1? %*’HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command “IsolatedCommand” = ‘”%1? %*’HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command “(Default)” = ‘”%1? %*’HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command “IsolatedCommand” – ‘”%1? %*’HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe” /START “%Program Files%\Mozilla Firefox\firefox.exe”‘HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe” /START “%Program Files%\Mozilla Firefox\firefox.exe” -safe-mode’HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe” /START “%Program Files%\Internet Explorer\iexplore.exe”‘HKEY..\..\..\..{RegistryKeys}HKEY_CLASSES_ROOT\.exe\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe” /START “%1? %*’HKEY_CLASSES_ROOT\exefile\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe” /START “%1? %*’
Use SpyHunter to Detect and Remove PC Threats
If you are concerned that malware or PC threats similar to Win 7 Home Security 2012 may have infected your computer, we recommend you start an in-depth system scan with SpyHunter. SpyHunter is an advanced malware protection and remediation application that offers subscribers a comprehensive method for protecting PCs from malware, in addition to providing one-on-one technical support service.
* See Free Trial offer below. EULA and Privacy/Cookie Policy.
Why can't I open any program including SpyHunter? You may have a malware file running in memory that kills any programs that you try to launch on your PC. Tip: Download SpyHunter from a clean computer, copy it to a USB thumb drive, DVD or CD, then install it on the infected PC and run SpyHunter's malware scanner.
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.