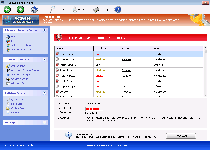
Windows Turnkey Console
Posted: June 4, 2012
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 42 |
| First Seen: | June 4, 2012 |
|---|---|
| Last Seen: | May 6, 2024 |
| OS(es) Affected: | Windows |
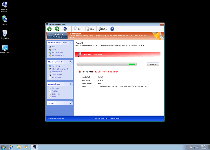
 Windows Turnkey Console is an amusingly accurately-named PC threat, given that, like other FakeVimes-based scamware, Windows Turnkey Console is closer to being your computer's jailer than its savior. While Windows Turnkey Console displays the same types of fraudulent security alerts and inaccurate system scan routines that similar variants of FakeVimes are known for, Windows Turnkey Console may also make direct attempts to cripple your computer's security features. All of Windows Turnkey Console's efforts are focused on getting you to buy its software, but SpywareRemove.com malware research suggest turning an about face and removing Windows Turnkey Console with a reputable anti-malware scanner, since Windows Turnkey Console's mere presence can subject your computer to continuous assault by browser hijacks and program-blocking attacks.
Windows Turnkey Console is an amusingly accurately-named PC threat, given that, like other FakeVimes-based scamware, Windows Turnkey Console is closer to being your computer's jailer than its savior. While Windows Turnkey Console displays the same types of fraudulent security alerts and inaccurate system scan routines that similar variants of FakeVimes are known for, Windows Turnkey Console may also make direct attempts to cripple your computer's security features. All of Windows Turnkey Console's efforts are focused on getting you to buy its software, but SpywareRemove.com malware research suggest turning an about face and removing Windows Turnkey Console with a reputable anti-malware scanner, since Windows Turnkey Console's mere presence can subject your computer to continuous assault by browser hijacks and program-blocking attacks.
Windows Turnkey Console: the Jailer with Bad Intel for Its Prisoners
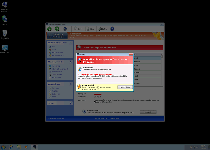
Windows Turnkey Console shares the same template as other recent variants of the FakeVimes family of rogue anti-malware scanners. As such, an initial look at Windows Turnkey Console might convince you that Windows Turnkey Console has the answer to all of your computer problems from viruses to phishing sites. Lamentably, though, SpywareRemove.com malware research team has confirmed that Windows Turnkey Console isn't able to provide any sort of accurate security-related information or delete hostile software from your hard drive. Windows Turnkey Console's substitutions for these feats are fake pop-up warnings and other forms of diagnostic information that always alert you to the supposed presence of nonexistent attackers and PC threats (such as keyloggers, Trojans or identity theft attacks).
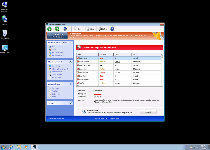
Along with these fake security efforts, Windows Turnkey Console may also block security-related features of Windows along with a variety of security programs, and SpywareRemove.com malware experts have also seen strong indications that Windows Turnkey Console may indulge itself in browser redirect attacks to promote harmful websites. Some of the main kinds of programs that Windows Turnkey Console can prevent you from using include:
- Popular brands of anti-virus and anti-malware scanners.
- The Windows Task Manager (a utility that allows you to view memory processes).
- The Windows Registry Viewer/Editor.
Enacting a Jailbreak from Windows Turnkey Console's PC Prison
Because many of Windows Turnkey Console's attacks make changes to the Windows Registry, Hosts file and other parts of Windows, SpywareRemove.com malware experts discourage manual attempts to revert Windows Turnkey Console's changes or delete Windows Turnkey Console. Industry-recognized anti-malware programs are able to remove all aspects of a Windows Turnkey Console infection whilst keeping the potential for damage to your operating system absolutely minimized.
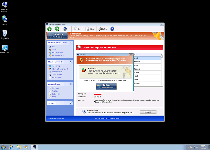
You may wish to register or disable Windows Turnkey Console before you run a scan to elicit Windows Turnkey Console's removal. Rogue anti-malware programs from the FakeVimes classification like Windows Turnkey Console are often able to be registered with the free code '0W000-000B0-00T00-E0020.' Disabling Windows Turnkey Console can also be accomplished by using the Windows Safe Mode feature or by booting your OS from a removable media-based source. SpywareRemove.com malware researchers note that analogous techniques can also be put in use to Windows Turnkey Console's clones such as Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0.
Use SpyHunter to Detect and Remove PC Threats
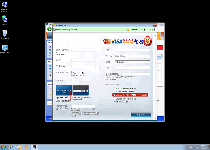
If you are concerned that malware or PC threats similar to Windows Turnkey Console may have infected your computer, we recommend you start an in-depth system scan with SpyHunter. SpyHunter is an advanced malware protection and remediation application that offers subscribers a comprehensive method for protecting PCs from malware, in addition to providing one-on-one technical support service.
* See Free Trial offer below. EULA and Privacy/Cookie Policy.
Why can't I open any program including SpyHunter? You may have a malware file running in memory that kills any programs that you try to launch on your PC. Tip: Download SpyHunter from a clean computer, copy it to a USB thumb drive, DVD or CD, then install it on the infected PC and run SpyHunter's malware scanner.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%APPDATA%\Protector-vkvq.exe
File name: Protector-vkvq.exeSize: 2.28 MB (2287104 bytes)
MD5: f715dd26b55f93d9f03e408213664e9f
Detection count: 68
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: June 4, 2012
%APPDATA%\Protector-rep.exe
File name: Protector-rep.exeSize: 2.08 MB (2083328 bytes)
MD5: 489543ca79af606a49436f37e3897e35
Detection count: 26
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: June 4, 2012
C:\rogueware samples\WintionalityChecker samples\Windows Turnkey console.exe
File name: Windows Turnkey console.exeSize: 2.28 MB (2287104 bytes)
MD5: 1c354ba1535e48e25787905ee5fef9db
Detection count: 7
File type: Executable File
Mime Type: unknown/exe
Path: C:\rogueware samples\WintionalityChecker samples\Windows Turnkey console.exe
Group: Malware file
Last Updated: May 6, 2024
Protector-[RANDOM CHARACTERS].exe
File name: Protector-[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\SystemRestore "DisableSR " = '1'HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avastsvc.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\afwserv.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ekrn.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\egui.exe "Debugger" = 'svchost.exe' HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msascui.exe "Debugger" = 'svchost.exe'HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe "Debugger" = 'svchost.exe'
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.