Windows Safety Checkpoint
Posted: April 27, 2012
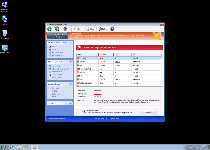
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 7 |
| First Seen: | April 27, 2012 |
|---|---|
| Last Seen: | February 6, 2019 |
| OS(es) Affected: | Windows |
 Windows Safety Checkpoint is marketed as a supposed anti-virus scanner that also includes a solid range of other security-related features, but in spite of its aesthetics, Windows Safety Checkpoint is just another rogue anti-virus application that displays fake warnings about Trojans, unauthorized network activity and other attacks that don't exist. Because Windows Safety Checkpoint is also derived from a family of scamware that have been noted for browser hijacks, attacks against unrelated security programs and attempts to disable Windows security features, SpywareRemove.com malware researchers consider Windows Safety Checkpoint to be an active danger to your PC that should be removed during an anti-malware scan immediately after noticing symptoms of the Windows Safety Checkpoint infection. Even though Windows Safety Checkpoint's primary purpose is to seduce you into throwing away your money on its purchasable version, the registered version of Windows Safety Checkpoint is just as lacking in value as its 'free' version, and buying Windows Safety Checkpoint should never be considered a viable solution to a Windows Safety Checkpoint infection or other computer problems.
Windows Safety Checkpoint is marketed as a supposed anti-virus scanner that also includes a solid range of other security-related features, but in spite of its aesthetics, Windows Safety Checkpoint is just another rogue anti-virus application that displays fake warnings about Trojans, unauthorized network activity and other attacks that don't exist. Because Windows Safety Checkpoint is also derived from a family of scamware that have been noted for browser hijacks, attacks against unrelated security programs and attempts to disable Windows security features, SpywareRemove.com malware researchers consider Windows Safety Checkpoint to be an active danger to your PC that should be removed during an anti-malware scan immediately after noticing symptoms of the Windows Safety Checkpoint infection. Even though Windows Safety Checkpoint's primary purpose is to seduce you into throwing away your money on its purchasable version, the registered version of Windows Safety Checkpoint is just as lacking in value as its 'free' version, and buying Windows Safety Checkpoint should never be considered a viable solution to a Windows Safety Checkpoint infection or other computer problems.
Windows Safety Checkpoint: Rogue AV Software That's Closer to Virus Than Anti-Virus Itself
Windows Safety Checkpoint draws its lineage from FakeVimes, a group of fake anti-virus applications that have been in distribution since 2010. In the past two years, Win32/FakeVimes scamware like Windows Safety Checkpoint have reappeared under new names again and again, with common examples of Windows Safety Checkpoint clones including Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0. Although some variants of Win32/FakeVimes-based rogue anti-virus bear some minor discrepancies in their appearances, SpywareRemove.com malware researchers have found that recent variants like Windows Safety Checkpoint are always identifiable by fake features like 'anti-phishing,' an 'Advanced Process Control' an 'All-In-One Suite,' an anti-virus scanner and various pop-up alerts.
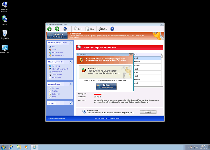
System scans, pop-ups and other forms of information that are provided by Windows Safety Checkpoint will always try to portray your PC as being under attack by an unrealistically large quantity of high-level PC threats, but such warnings can be safely ignored as fraudulent. Besides being incapable of detecting real Trojans, viruses or other PC threats, Windows Safety Checkpoint is also incapable of deleting any type of malicious software – even if you waste money on its purchasable version. Nevertheless, SpywareRemove.com malware experts note that registering Windows Safety Checkpoint for free with the code '0W000-000B0-00T00-E0020' can sometimes be useful for removing Windows Safety Checkpoint with less interference.
The Full Checklist of Windows Safety Checkpoint's Aggressions
Fake security pop-ups, system scans and similar types of inaccurate system analyses can always be considered Windows Safety Checkpoint's raison d'être, but some functions of Windows Safety Checkpoint that are secondary to its primary purpose can actually be of greater danger than its primary attacks. Like other fake anti-virus applications based on Win32/FakeVimes, Windows Safety Checkpoint may also enact hostile behavior against legitimate security programs and some Windows features, such as:
- Windows Safety Checkpoint may disable the UAC, which SpywareRemove.com malware experts stress is a high-priority security attack that allows PC threats like Windows Safety Checkpoint to make unauthorized changes to your computer.
- Windows Safety Checkpoint may hijack your web-browsing activities, especially for the sake of redirecting you from reputable search engines to suspicious or outright hostile ones. Such hijacks are likely to function in all types of web browsers due to a Trojan changing the Hosts file.
- Windows Safety Checkpoint may also prevent you from using real security programs, including Task Manager, while Windows Safety Checkpoint is active. In cases where this prevents you from running an anti-malware scan to delete Windows Safety Checkpoint, SpywareRemove.com malware analysts can recommend Safe Mode, a boot from a network-shared drive or a boot from a removable drive to launch Windows without Windows Safety Checkpoint getting in the way.
Use SpyHunter to Detect and Remove PC Threats
If you are concerned that malware or PC threats similar to Windows Safety Checkpoint may have infected your computer, we recommend you start an in-depth system scan with SpyHunter. SpyHunter is an advanced malware protection and remediation application that offers subscribers a comprehensive method for protecting PCs from malware, in addition to providing one-on-one technical support service.
* See Free Trial offer below. EULA and Privacy/Cookie Policy.
Why can't I open any program including SpyHunter? You may have a malware file running in memory that kills any programs that you try to launch on your PC. Tip: Download SpyHunter from a clean computer, copy it to a USB thumb drive, DVD or CD, then install it on the infected PC and run SpyHunter's malware scanner.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%APPDATA%\Protector-ucxk.exe
File name: Protector-ucxk.exeSize: 1.86 MB (1865216 bytes)
MD5: e2b9f9e66abbb94a9477ca14a3ad39d8
Detection count: 97
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: April 27, 2012
%APPDATA%\Protector-obux.exe
File name: Protector-obux.exeSize: 1.86 MB (1860608 bytes)
MD5: 6d3b5309cfb72ace5320a827d09a91df
Detection count: 76
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: April 27, 2012
%AppData%\Inspector-[RANDOM CHARACTERS].exe
File name: %AppData%\Inspector-[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AppData%\Protector-[RANDOM CHARACTERS].exe
File name: %AppData%\Protector-[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "ID" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "rudbxijemb"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = "2012-2-17_2"HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_ERROR_PAGE_BYPASS_ZONE_CHECK_FOR_HTTPS_KB954312HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\zapsetup3001.exe HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\divx.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mostat.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\platin.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\_avp32.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\_avpcc.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ashDisp.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tapinstall.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\zapsetup3001.exe
Additional Information
| # | Message |
|---|---|
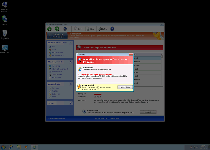
| 1 | Error Trojan activity detected. System data security is at risk. |
| 2 | Warning Firewall has blocked a program from accessing the Internet C:\program files\internet explorer\iexplore.exe is suspected to have infected your PC. This type of virus intercepts entered data and transmits them to a remote server. |



Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.