Windows Risk Minimizer
Posted: March 13, 2012
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
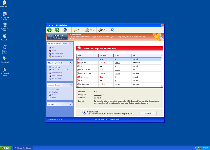
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 9 |
| First Seen: | March 13, 2012 |
|---|---|
| Last Seen: | January 8, 2020 |
| OS(es) Affected: | Windows |
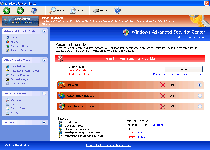 Windows Risk Minimizer is a rogue anti-malware program that does not do what its name implies. Instead of detecting and removing PC threats, Windows Risk Minimizer will create vulnerabilities on your computer and present fake detection information. This shouldn't come as any surprise to anyone who's had a look at Windows Risk Minimizer and is familiar with the FakeVimes family, however, since Windows Risk Minimizer is cloned straight from other variants of that family's scamware. Unwarranted application blacklisting, browser redirects, pop-ups and fake scans can all be used during Windows Risk Minimizer's siege against your PC. SpywareRemove.com malware researchers recommend that you hold tightly onto your money and delete Windows Risk Minimizer with a real anti-malware application as soon as you catch a whiff of the Windows Risk Minimizer scam.
Windows Risk Minimizer is a rogue anti-malware program that does not do what its name implies. Instead of detecting and removing PC threats, Windows Risk Minimizer will create vulnerabilities on your computer and present fake detection information. This shouldn't come as any surprise to anyone who's had a look at Windows Risk Minimizer and is familiar with the FakeVimes family, however, since Windows Risk Minimizer is cloned straight from other variants of that family's scamware. Unwarranted application blacklisting, browser redirects, pop-ups and fake scans can all be used during Windows Risk Minimizer's siege against your PC. SpywareRemove.com malware researchers recommend that you hold tightly onto your money and delete Windows Risk Minimizer with a real anti-malware application as soon as you catch a whiff of the Windows Risk Minimizer scam.
Counting Out all the Ways That Windows Risk Minimizer Lies to You
Going by appearances alone, Windows Risk Minimizer acts like an anti-malware program that's holding an immense tide of PC threats back from ravaging your computer. Although Windows Risk Minimizer will create error messages and scans that recommend that you apply your funds on the full version of Windows Risk Minimizer for complete threat removal, this is the absolute last thing that you should do. Warnings and other pop-ups from Windows Risk Minimizer, as well as its scans, are always designed to create inaccurate infection alerts that make you contemplate panicking and throwing your money at Windows Risk Minimizer just to make these threatening messages vanish into the ether.
However, just like every other example of fake anti-virus software from Rogue.VirusDoctor, Windows Risk Minimizer can't detect PC threats or remove them, even if you waste money on Windows Risk Minimizer.
Other members of the same family as Windows Risk Minimizer include Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0.
How to Minimize the Harm That Windows Risk Minimizer Can Do to Your PC
Until you're able to use suitable anti-malware programs for Windows Risk Minimizer's removal, you may also want to watch for other symptoms of Windows Risk Minimizer's attacks. In addition to its typical fake security functions, Windows Risk Minimizer will also make attacks on your PC to promote itself and reduce your computer's security, such as:
- Redirects may take your browser to Windows Risk Minimizer's site or censor PC security sites.
- Windows Risk Minimizer may also block security programs, such as the Task Manager, with fake warnings or replace the program in question with its own poor substitute.
Under most circumstances, these attacks require you to disable Windows Risk Minimizer, which can easily be done via standard anti-malware practices, before you can delete Windows Risk Minimizer and associated PC threats.



Use SpyHunter to Detect and Remove PC Threats
If you are concerned that malware or PC threats similar to Windows Risk Minimizer may have infected your computer, we recommend you start an in-depth system scan with SpyHunter. SpyHunter is an advanced malware protection and remediation application that offers subscribers a comprehensive method for protecting PCs from malware, in addition to providing one-on-one technical support service.
* See Free Trial offer below. EULA and Privacy/Cookie Policy.
Why can't I open any program including SpyHunter? You may have a malware file running in memory that kills any programs that you try to launch on your PC. Tip: Download SpyHunter from a clean computer, copy it to a USB thumb drive, DVD or CD, then install it on the infected PC and run SpyHunter's malware scanner.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:Protector-gtk.exe
File name: Protector-gtk.exeSize: 2.1 MB (2105246 bytes)
MD5: 1a30a36401f4374a5a464ff58bca3ef0
Detection count: 85
File type: Executable File
Mime Type: unknown/exe
Group: Malware file
Last Updated: January 8, 2020
%AppData%\npswf32.dll
File name: %AppData%\npswf32.dllFile type: Dynamic link library
Mime Type: unknown/dll
Group: Malware file
%AppData%\Inspector-[RANDOM CHARACTERS].exe
File name: %AppData%\Inspector-[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%CommonPrograms%\Windows Risk Minimizer.lnk
File name: %CommonPrograms%\Windows Risk Minimizer.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%DesktopDir%\Windows Risk Minimizer.lnk
File name: %DesktopDir%\Windows Risk Minimizer.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
Registry Modifications
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"
Additional Information
| # | Message |
|---|---|
| 1 | Error Keylogger activity detected. System information security is at risk. It is recommended to activate protection and run a full system scan. |
| 2 | Warning Firewall has blocked a program from accessing the Internet C:program filesinternet exploreriexplore.exe is suspected to have infected your PC. This type of virus intercepts entered data and transmits them to a remote server. |
| 3 | Warning! Identity theft attempt Detected Hidden connection IP: 58.82.12.124 Target: Your passwords for sites |
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.