Windows Protection Master
Posted: February 12, 2012
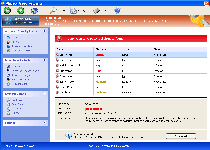
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 54 |
| First Seen: | February 12, 2012 |
|---|---|
| Last Seen: | May 6, 2024 |
| OS(es) Affected: | Windows |
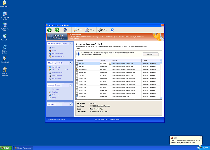
 Windows Protection Master holds membership in a broad group of fake anti-malware and debugging scanners that imitate Microsoft Security Essentials by providing fraudulent error reports. These reports are delivered as a way to scam victims into spending money on Windows Protection Master's complete version to fix nonexistent issues and should always be disregarded as irrelevant and deceptive in nature. Because rogue debuggers from Windows Protection Master's family have been noted for their ability to disable many types of security and system analysis applications, SpywareRemove.com malware research team recommends that you treat Windows Protection Master as a severe threat to your computer's security until you've removed all of Windows Protection Master's components, ideally with a competent anti-malware scanner.
Windows Protection Master holds membership in a broad group of fake anti-malware and debugging scanners that imitate Microsoft Security Essentials by providing fraudulent error reports. These reports are delivered as a way to scam victims into spending money on Windows Protection Master's complete version to fix nonexistent issues and should always be disregarded as irrelevant and deceptive in nature. Because rogue debuggers from Windows Protection Master's family have been noted for their ability to disable many types of security and system analysis applications, SpywareRemove.com malware research team recommends that you treat Windows Protection Master as a severe threat to your computer's security until you've removed all of Windows Protection Master's components, ideally with a competent anti-malware scanner.
Windows Protection Master: Scamware That's Protective Only for Itself
Windows Protection Master was first noted by many PC security companies in February of 2012, although Windows Protection Master's family has been in existence since early 2011. Some of the many clones from the same family as Windows Protection Master include Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0. These applications use a combination of fake percentile-based ratings of your computer's safety and a feature set that imitates the appearance of the look of Microsoft Security Essentials to make you think that nonexistent attacks against your PC are occurring on an ongoing basis.
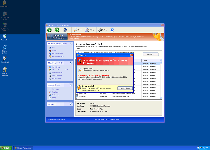
However, SpywareRemove.com malware analysts stress that Windows Protection Master, like other products from the FakeVimes group, isn't able to detect or eliminate real problems with your PC. Hence, if you see warning messages that resemble the following samples, you should ignore them as fraudulent examples of Windows Protection Master's scam:
System Security Warning
Attempt to modify register key entries is detected. Register entries analysis is recommended.
Warning!
Location: [Application file path]
Viruses: Backdoor.Win32.Rbot
Warning!
Name: [Application file name]
Name: [Application file path]
Application that seems to be a key-logger is detected. System information security is at risk. It is recommended to enable the security mode and run total System scanning.
Warning! Database update failed!
Database update failed!
Outdated viruses databases are not effective and can't [sic] guarantee adequate protection and security for your PC!
Click here to get the full version of the product and update the database!
Mastering a Defense Against Windows Protection Master's Attacks
Windows Protection Master and similar PC threats have also received attention for their ability to detect and close processes that they deem to be undesirable; in most cases, such processes are noted to be related to system security, analysis or the removal of malicious software like Windows Protection Master. SpywareRemove.com malware research team has found that some of the programs that Windows Protection Master may close include:
- Windows monitoring tools like Task Manager that could detect or close malicious processes like Windows Protection Master's own memory process
- Registry tools like the Registry Editor that could be used to remove Windows Protection Master's automatic startup entries.
- Torrent and other types of mass-downloading applications.
- Webcam utilities.
- Photoshop-related applications and other types of Adobe programs.
- Certain types of e-mail clients, including Outlook.
- Some web browsers (such as Opera).
- Popular brands of instant messaging clients.
- Script packages such as Flash and Java.
- Google-brand products.
- iTunes.
Because Windows Protection Master may enumerate your memory processes on a constant basis, Windows Protection Master may also use up excessive system resources and cause performance issues. Nonetheless, although Windows Protection Master and its clones are able to attack a wide range of applications, SpywareRemove.com malware researchers also note that Windows Protection Master hasn't been found to attack most types of anti-malware scanners. Thus, a competent anti-malware program should be able to delete Windows Protection Master without encountering issues.

Use SpyHunter to Detect and Remove PC Threats
If you are concerned that malware or PC threats similar to Windows Protection Master may have infected your computer, we recommend you start an in-depth system scan with SpyHunter. SpyHunter is an advanced malware protection and remediation application that offers subscribers a comprehensive method for protecting PCs from malware, in addition to providing one-on-one technical support service.
* See Free Trial offer below. EULA and Privacy/Cookie Policy.
Why can't I open any program including SpyHunter? You may have a malware file running in memory that kills any programs that you try to launch on your PC. Tip: Download SpyHunter from a clean computer, copy it to a USB thumb drive, DVD or CD, then install it on the infected PC and run SpyHunter's malware scanner.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%APPDATA%\Inspector-cux.exe
File name: Inspector-cux.exeSize: 1.98 MB (1985024 bytes)
MD5: de46e3c96422246c44304996eb4d80ed
Detection count: 73
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: February 14, 2012
%APPDATA%\Inspector-lbe.exe
File name: Inspector-lbe.exeSize: 1.98 MB (1988096 bytes)
MD5: 4941fcc45213c87accaddb8303d66d0f
Detection count: 59
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: February 14, 2012
%APPDATA%\Inspector-trb.exe
File name: Inspector-trb.exeSize: 1.98 MB (1989632 bytes)
MD5: 65126d03bfb1e03822330f5178ccafc3
Detection count: 11
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: February 14, 2012
C:\rogues\Windows Protection Master.exe
File name: Windows Protection Master.exeSize: 1.98 MB (1985024 bytes)
MD5: 456d83a75d1e96a3787c0d92f10622c3
Detection count: 9
File type: Executable File
Mime Type: unknown/exe
Path: C:\rogues\Windows Protection Master.exe
Group: Malware file
Last Updated: May 6, 2024
%APPDATA%\Inspector-mhk.exe
File name: Inspector-mhk.exeSize: 1.98 MB (1989632 bytes)
MD5: 3a72fd214b076f343167b45633347061
Detection count: 5
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: January 8, 2020
[RANDOM].exe
File name: [RANDOM].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AllUsersProfile%\Start Menu\Programs\Windows Protection Master\Windows Protection Master.lnk
File name: %AllUsersProfile%\Start Menu\Programs\Windows Protection Master\Windows Protection Master.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%AppData%\Inspector-[random three characters].exe
File name: %AppData%\Inspector-[random three characters].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AppData%\NPSWF32.dl
File name: %AppData%\NPSWF32.dlMime Type: unknown/dl
Group: Malware file
%AppData%\result.db
File name: %AppData%\result.dbMime Type: unknown/db
Group: Malware file
%UserProfile%\Desktop\Windows Protection Master.lnk
File name: %UserProfile%\Desktop\Windows Protection Master.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%StartMenu%\Programs\Windows Protection Master.lnk
File name: %StartMenu%\Programs\Windows Protection Master.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
Registry Modifications
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Windows Protection MasterHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\adaware.exe "Debugger"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\belt.exe "Debugger"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\deputy.exe "Debugger"HKEY_LOCAL_MACHINE\Software\[APPLICATION]\Microsoft\Windows\CurrentVersion\Uninstall..{Uninstaller}HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Uninstall\[RANDOM]_is1
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.